Cybersecurity startup trends of 2022
In 2021, entrepreneurs raised more than $21 billion to combat data breaches and vulnerabilities. Now, three key trends are driving Bessemer’s future cyber investments.
Cybersecurity is finally taking its rightful place at the center stage of the global business and geopolitical community. Just a few short years since data privacy regulations such as GDPR and CCPA came into play, the international community has seen some of the most high profile attacks make their mark in the media and the boardroom. Whether it was the hundred million dollar fallout of the SolarWinds breach, the Colonial Pipeline hack that resulted in hour-long lines at the gas pumps in the southeast, or the JBS ransomware that wiped out one fifth of US beef capacity, cybersecurity showed that it impacts every industry and just about anyone with a digital footprint.
At the same time, 2021 proved to be the most prolific year for cybersecurity venture investing, highlighting the appetite for new approaches in the space. Over $21 billion was raised by cybersecurity companies, shattering 2020’s record of $8.9 billion. Fueling this growth has been a record number of growth-stage rounds, including 27 funding rounds of $200 million or more. A new herd of cybersecurity unicorns have emerged featuring names such as Wiz, Orca, Lacework, Claroty, BigID, and Axonius.
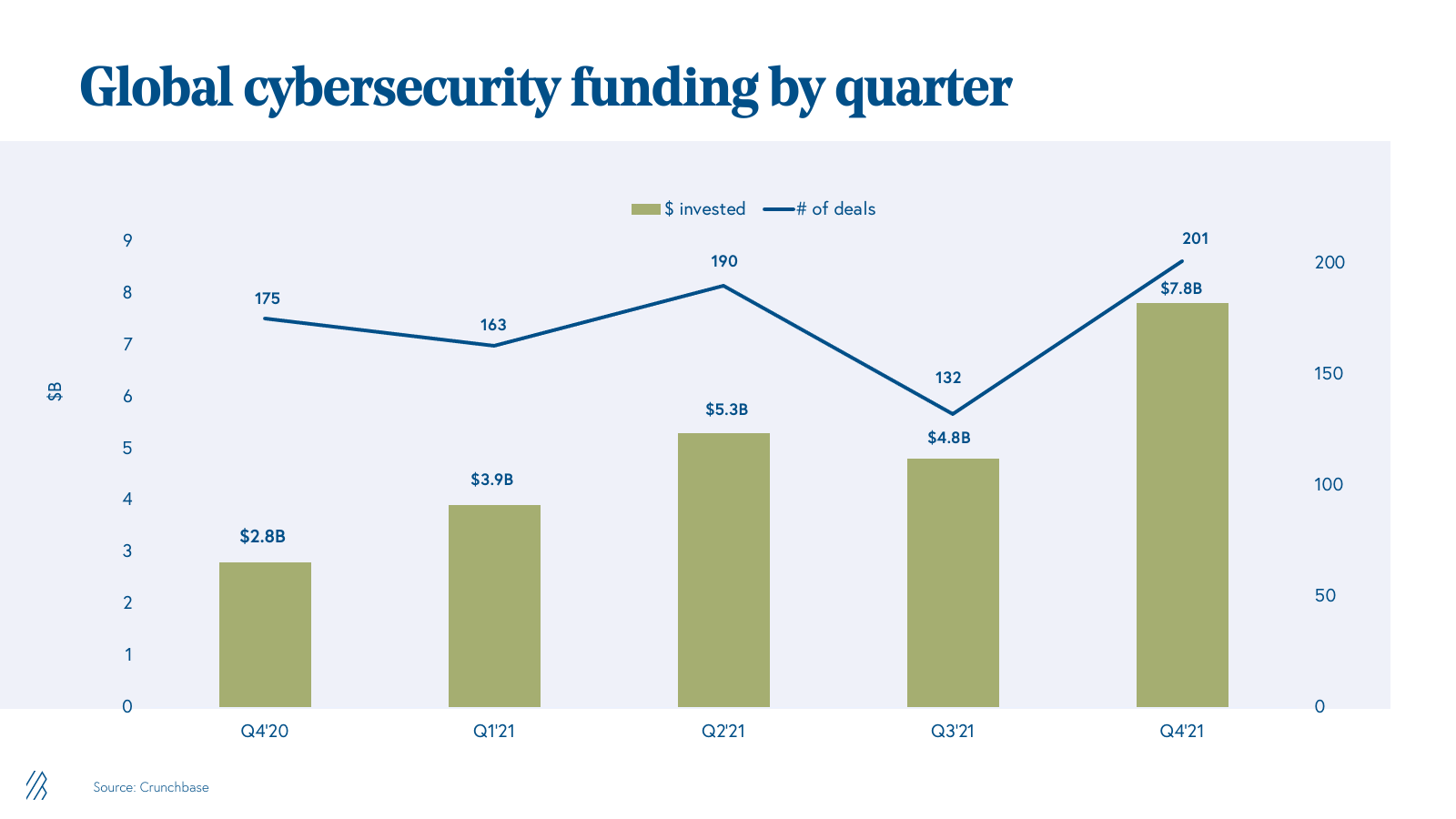
Today’s funding environment reflects the demand and growing opportunity for startups to grow into large, independent enterprises. For example: In the past, a small number of large incumbents such as Checkpoint, Palo Alto Networks, Symantec and Cisco completely dominated the market. Back then, the best outcome for a startup was getting acquired by one of these major platforms. Yet the emergence of new categories, the quick pace of change, and CISOs’ increased willingness to purchase security from startups, makes it more feasible than ever for a tiny startup to scale into a new cyber giant. These dark horses (in other words, unicorns!) are leading security platforms that are dominant in their niche and aim to enter the public markets.
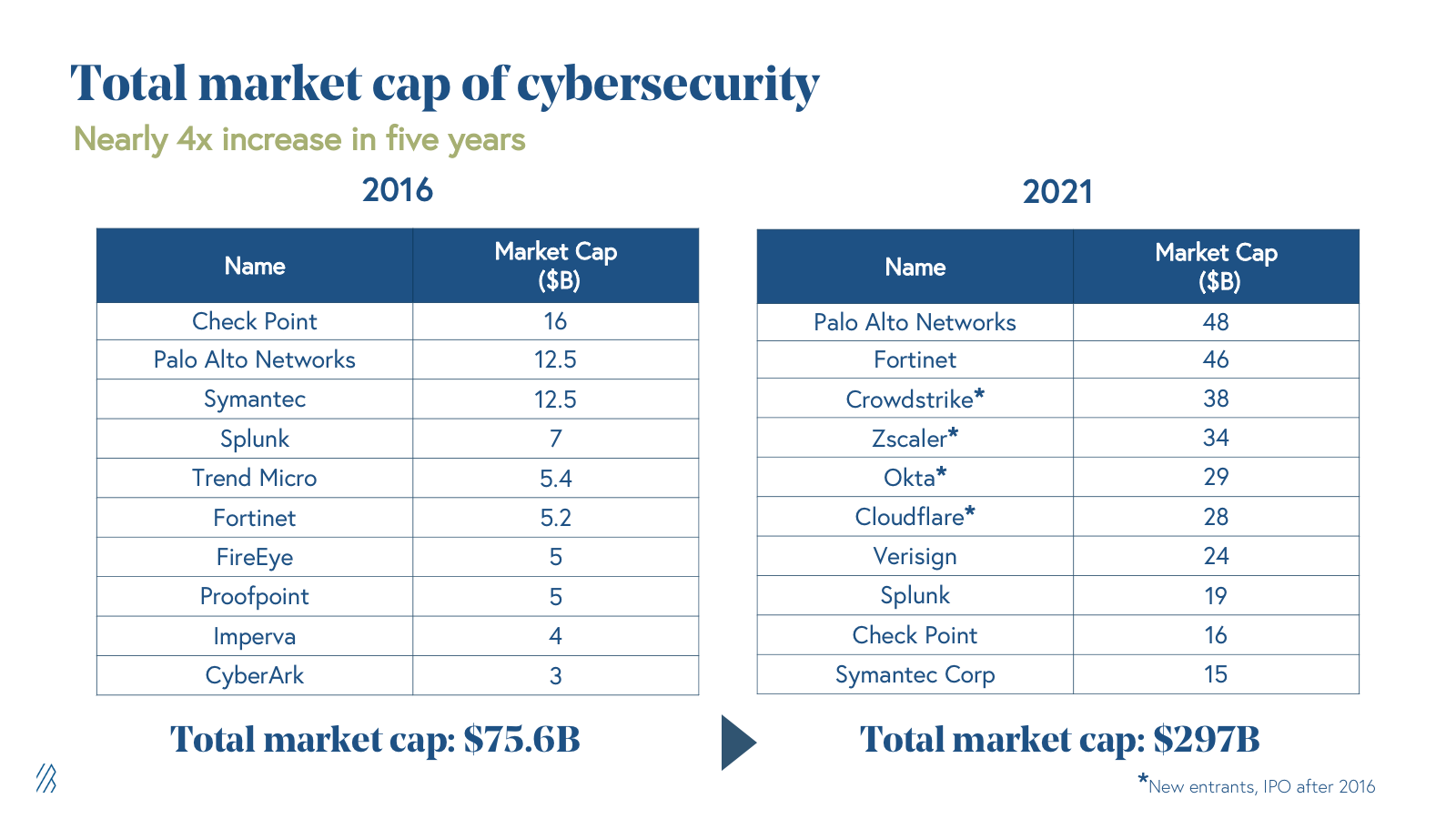
Case in point: Crowdstrike, Okta, Cloudflare, ZScaler, and Splunk are all examples of new companies that are among the top 10 largest security companies today. Even factoring in the recent public market decline, the level of dynamism in the cyber sector, as demonstrated by the level of change in the top 10 companies, remains high.
Still, the cybersecurity struggles of 2021 will continue in 2022. As software is the largest sector weighting in the S&P 500, disrupting every industry from automotive (Tesla) to healthcare (Teladoc), the threat landscape is only getting more complex. Today’s global economy will only grow more dependent on the evolution of how enterprises, governments, and individuals protect themselves from cyber threats. In addition, the rise of a remote and hybrid economy has made it easier for malicious attackers to do harm while cryptocurrencies have made it easier to facilitate untraceable ransom payments. Considering these factors, we’re zeroing in on three macro trends that’ll impact cyber investing in 2022.
Trend 1: Security spend will move to the forefront for businesses in all sectors
Cybersecurity is a massive market with over $150 billion in annual spend and has consistently accounted for 6% of total IT spend. On a vertical basis, however, security spend varies widely, with cloud companies spending the most on security at 9.5% of overall IT budget. We anticipate that other vertical industries will start to catch up to cloud companies and invest more heavily in cybersecurity, as these industries increasingly digitize and shift their offerings over to software solutions.
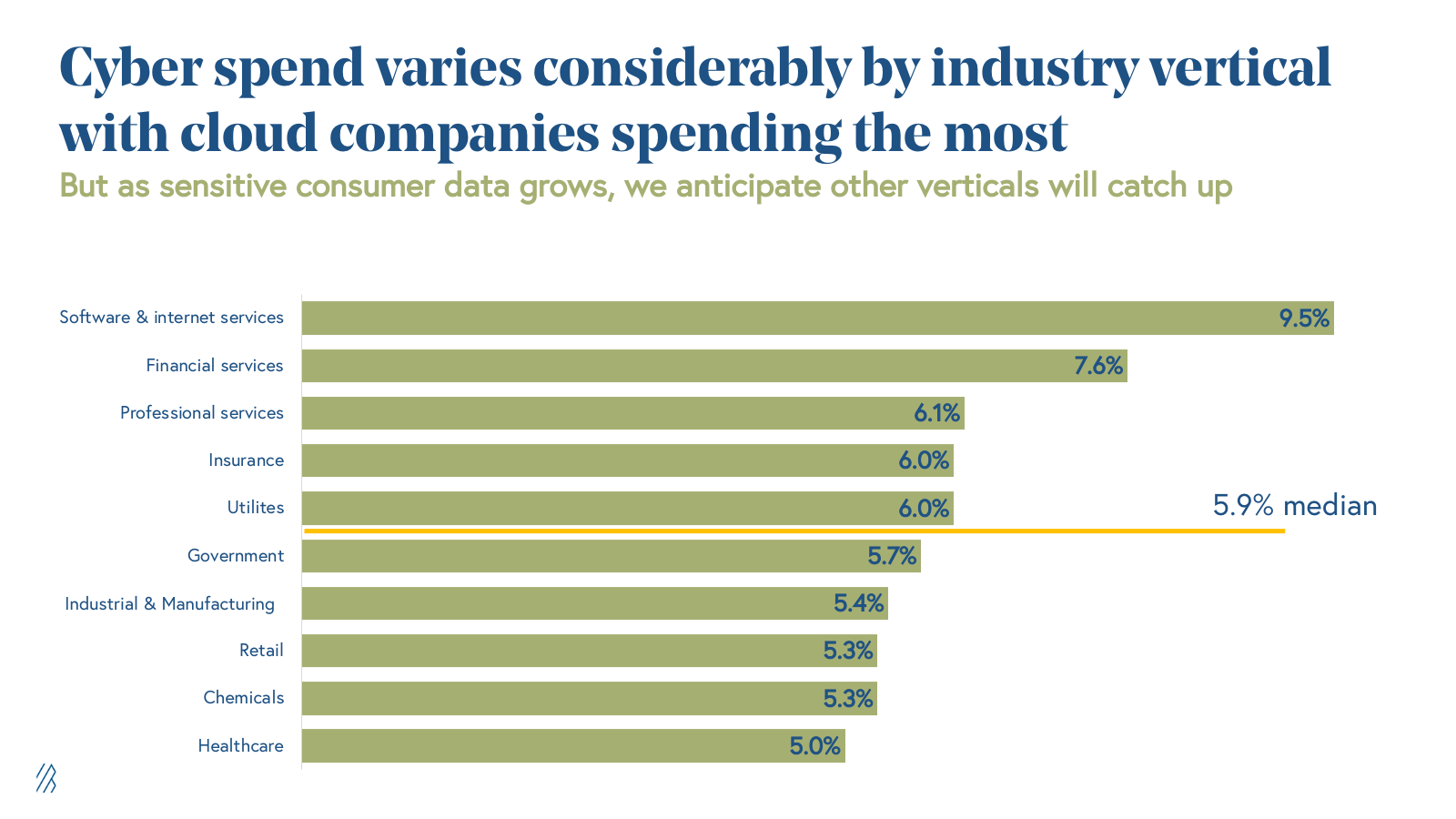
There are a couple of main drivers we see for this change in security spending from CISOs. First, increased privacy regulations like GDPR and CCPA are requiring all companies that deal with consumer data to have better safeguards or face the risk of costly fines and reputation loss. This puts pressure on industries such as financial services, healthcare, and retail to invest more heavily in cybersecurity, given the vast amounts of sensitive consumer data they deal with. Second, historically offline-industries, including supply chain and logistics, utilities, consumer electronics, and medical technology, are bringing their critical infrastructure to the cloud through IoT devices and edge computing, creating a new threat vector for bad actors and introducing potentially devastating consequences. Last year’s hack of a Florida water treatment plant, for example, highlighted that cyber crime does not just impact a company’s bottom-line, but could also pose a much greater threat to public health. As more of these businesses and public entities move to the cloud, increased spend on cybersecurity will be an inevitable imperative.
Cybercrime poses a threat to public health.
As such, we see opportunities for vertical-specific security solutions to emerge that better address the needs of these businesses. Traditionally, cybersecurity solutions have been horizontal, enterprise applications, but by taking a vertical approach, companies can focus on building the right types of integrations and addressing the specific pain points of each unique industry. Claroty, for example, has built a platform that integrates directly to industrial IoT devices to provide real-time monitoring of anomalies in operational networks, helping to protect infrastructure, including water treatment facilities and electrical grids. With their recent acquisition of Medigate, Claroty will be able to monitor medical devices, as well. Historically, healthcare has been one of the top targets for cyber attacks, considering the vast troves of sensitive patient and customer data. And medical devices are one of the vulnerable entry points attackers have exploited over the years. However, with improved security solutions serving industries early in their digitization, an IoT security platform with vertical-specific device integrations would be better equipped to address these complex issues (compared to horizontal network security solutions unfamiliar with these medical-specific endpoints). The verticalization of cybersecurity solutions is on the rise in 2022, and we see massive opportunities for entrepreneurs to build the go-to solution for industries increasing their software spend.
Trend 2: The institutionalization of ransomware
Ransomware has quickly become the most popular attack scheme, now accounting for 30% of all cyber attacks. And the rates are only growing as bad actors have access to widely available tools and techniques to perpetrate an attack. In fact, criminal organizations sell Ransomware-as-a-Service (RaaS) kits which are promoted and sold on the dark web using the same marketing and sales tactics that legitimate businesses use on the regular web. These solutions can be deployed at scale and make it cost effective to not only target large enterprises but also mid-sized organizations and even small businesses that usually lack dedicated security expertise.
Ransomware accounts for 30% of all cyber attacks.
Ransomware can take on many forms, infiltrating an organization through a supply chain attack, zero-day vulnerability, or phishing email. While there are many different techniques, they all share the goal of taking control of a host’s systems and demanding money from the victim.
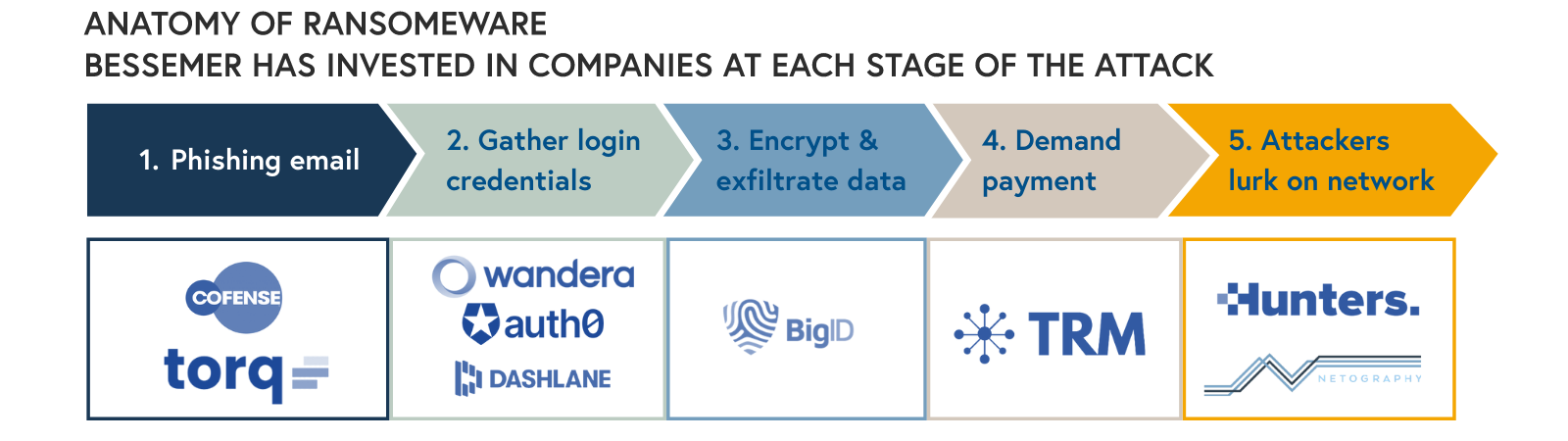
For example, if we looked at the typical phishing scam, a ransomware attack can be broken down into five main components:
- A phishing email tricks employees into opening an attachment or clicking on a link that downloads malicious software.
- Once access is gained, the attacker uses tools to gather login credentials and spread laterally throughout the network as it attempts to identify high value assets such as AWS admin passwords.
- Then, a hacker encrypts and exfiltrates high value data, such as personal identifiable information, source code, and other critical data.
- At this point, they demand payment in Bitcoin or another digital currency in exchange for decryption keys and promise not to leak exfiltrated data.
- Finally, attackers often lurk on the network even after they’ve been paid.
Each of these steps represents an opportunity for a cybersecurity company to offer protection and Bessemer has invested in several companies addressing these vulnerabilities. For example, the first step in protecting against a ransomware attack is to ensure that the business knows where sensitive data is stored. Our company, BigID, helps enterprises take inventory of sensitive customer personal information across both cloud and on-premise environments and apply the proper access controls. Another example is Netography, whose cloud-based network detection engine can monitor encrypted network traffic and detect malicious traffic in real time. A solution like Netography can help security spot when attackers are spreading through their network during an attack and ensure they are not lingering about after one.
Still, ransomware protection as a category has room to grow and evolve. As more enterprises move to cloud-native and multi-cloud environments, data is becoming more widely distributed across an organization and demands better data security, tokenization, and encryption solutions. There is also a greater need for security awareness and email security solutions, as phishing continues to be the most popular entry point for a ransomware attack. With over 500 million attempted attacks in 2021, these concerns are top of mind for CISOs and moving up in the priority list.
Trend 3: The Great Consolidation is afoot
CISOs are looking for more comprehensive security platforms as infrastructure moves away from on-premise.
As enterprises move to the cloud and embrace remote work, legacy on-premise security solutions are no longer cutting it. The traditional security model of using firewalls and robust network security to keep out nefarious groups and hackers is quickly breaking down. This is especially the case as data is stored with third-party cloud providers and employees access these resources from outside the enterprise’s four walls.
CISOs are looking for more comprehensive security platforms.
On-premise security is also becoming more expensive. Recent ransomware attacks, like SolarWinds, have highlighted the need to maintain multiple month’s worth of telemetry to trace the full impact of an attack. More telemetry equates to more storage, which is putting budget pressure on CISOs as most on-premise vendors price based on storage. Now, CISOs are beginning to seek out more innovative, cloud-native vendors to find the right solutions with the right price.
In response, a flood of new startups has entered the market, offering dozens of new point solutions for every security need. But this thriving startup environment is driving a new set of challenges. Without a doubt, the cybersecurity industry is going through it’s own evolution— many legacy companies are not innovating fast enough, CISOs don’t have the bandwidth to keep up with all the new options, and even Gartner and analysts cannot distinguish between vendors, as many of these companies use the same marketing jargon. In fact, sometimes even the websites look exactly the same!
The implication for startups is that it’s not just about having the best tech solution, but also consolidating and orchestrating other siloed solutions to help security teams find the signal in the noise. As cybersecurity spend increases, CISOs will prune their long list of current security vendors and will pay a premium for those that help reduce alert fatigue and prioritize the most pressing issues. Take Axonius: their platform connects to all existing security tools and consolidates their information into a single pane of glass. Teams then have full visibility into the enterprise to manage their security posture, without having to manually piece together the separate insights of their tools.
Ultimately, this push to consolidate solutions and correlate signals from many security tools in one place is leading many enterprises to adopt a cloud-based security information and event management system (SIEM).
Legacy on-prem SIEM solutions are proving to be too rigid and expensive to maintain as security teams embrace cloud-based products and alert data volumes continue to grow. By leveraging a cloud data warehouse (e.g. Snowflake, Databricks) instead, it is easier to scale storage at a predictable cost and centralize security data. With a cloud-data warehouse, security tools can also capture business data that can provide additional context. For instance, Hunters.ai offers organizations an open extended and response platform (XDR) that sits on top of a cloud data warehouse and ingests signals across both security tools and saas apps (like Okta and Workday), running security analytics across these sources to identify threats in real-time. By leveraging the economic advantages of cloud data warehouses, Hunters delivers high performance at a predictable cost. Companies like Hunters are making it simpler for security teams to correlate signals across their software stack and make the transition to cloud-native approaches to security.
It is time to innovate in cybersecurity
As nearly every industry is rethinking their digital presence and shifting their infrastructure to the cloud, data privacy and security will persist as top issues for CISOs and everyday people. Ransomware isn’t going anywhere anytime soon, but we do believe that the ubiquity of data security issues in 2021 has elevated cybersecurity as a top imperative for enterprises across every sector. If you’re building a startup, now is a great time to serve new industries, capitalize on the momentum, and make the world a more secure place to work and live. If you’re a founder and these themes resonated with you, please let us know by emailing us at karp@bvp.com, alex@bvp.com, and ctarnopol@bvp.com.